AWS CloudTrail Logs
Please use this integration guide to configure CloudTrail log alerts so they can be received in Squadcast. This integration should be used only for getting CloudTrail log alerts via a SNS endpoint.
For CloudTrail alerts, use the AWS CloudTrail via CloudWatch integration.
For regular AWS CloudWatch alarms (like EC2 alerts), use the AWS CloudWatch Integration.
Using AWS CloudTrail Logs via SNS as an Alert Source
(1) From the navigation bar on the left, select Services. Pick the applicable Team from the Team-picker on the top. Next, click on Alert Sources for the applicable Service
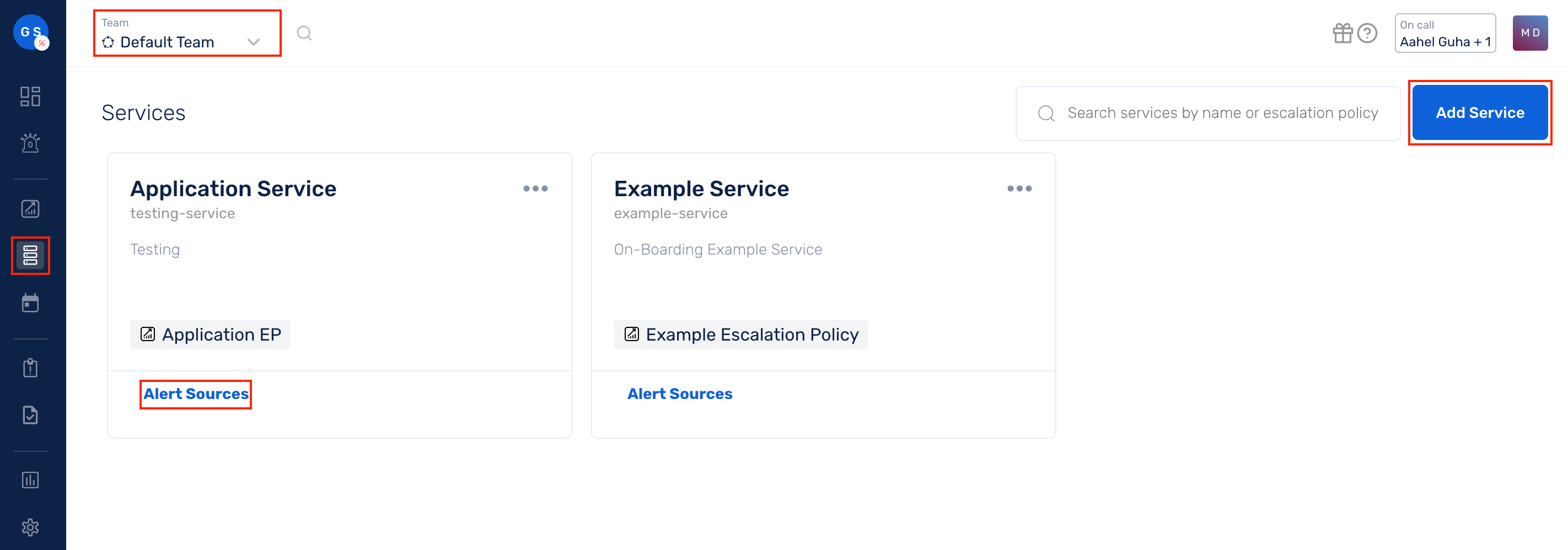
(2) Search for AWS CloudTrail Logs via SNS from the Alert Source drop-down and copy the Webhook URL
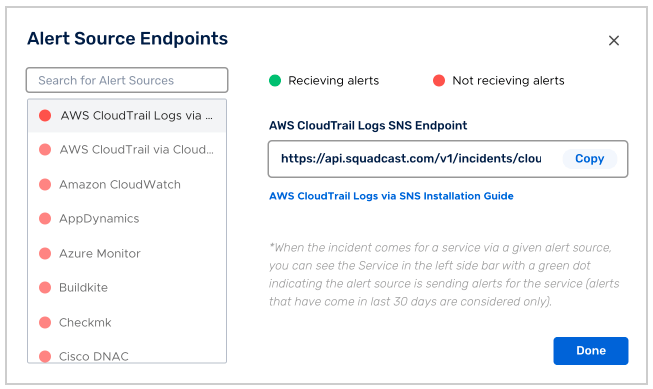
For an Alert Source to turn active (indicated by a green dot - Receiving alerts against the name of the Alert Source in the drop-down), you can either generate a test alert or wait for a real-time alert to be generated by the Alert Source.
An Alert Source is active if there is a recorded incident via that Alert Source for the Service in the last 30 days.
Create CloudTrail logs Endpoint in AWS SNS
Now log in to your AWS account and proceed to SNS.
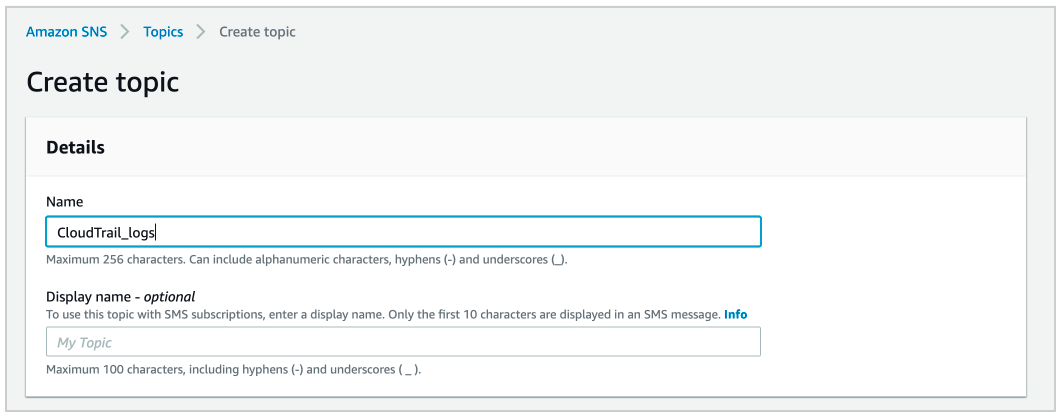
Click on “Create topic” to get “Create new topic” dialog box. Fill in the details as per your requirements and then click on “Create topic”
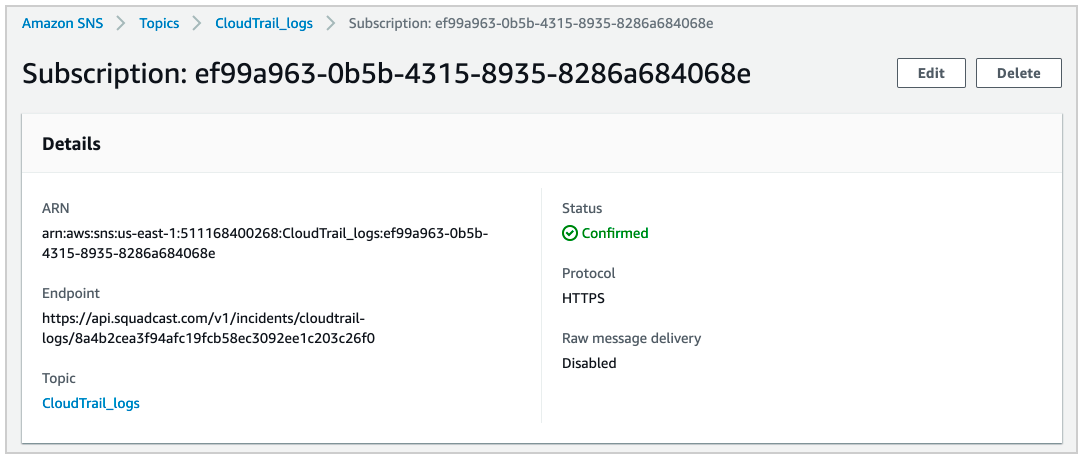
Now inside the topic, click on “Create subscription” to get “Create subscription” dialog box. Select the protocol as “HTTPS” and in the endpoint enter the URL you obtained from previous step. Finally, click on “Create subscription” to create the subscription.
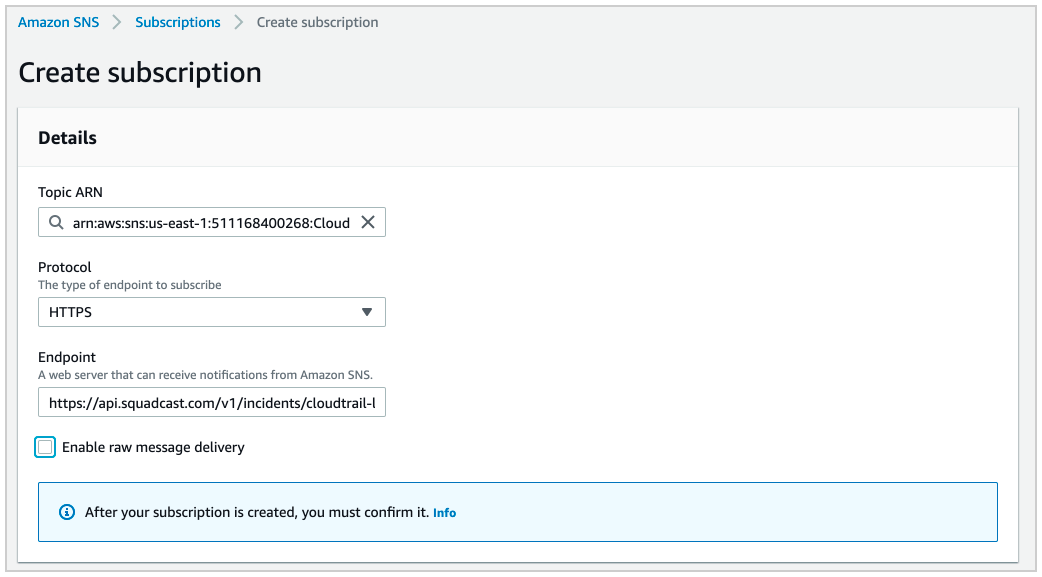
The “Subscription ID” for the subscription should to “Confirmed” immediately change from “PendingConfirmation”. Click on the refresh button to verify the same.
Then you can configure your CloudTrail log alerts and assign this topic as the notification option and you are good to go.