Graylog
Follow the steps below to configure a service so as to extract its related alert data from Graylog.
Squadcast will then process this information to create incidents for this service as per your preferences.
Using Graylog as an Alert Source
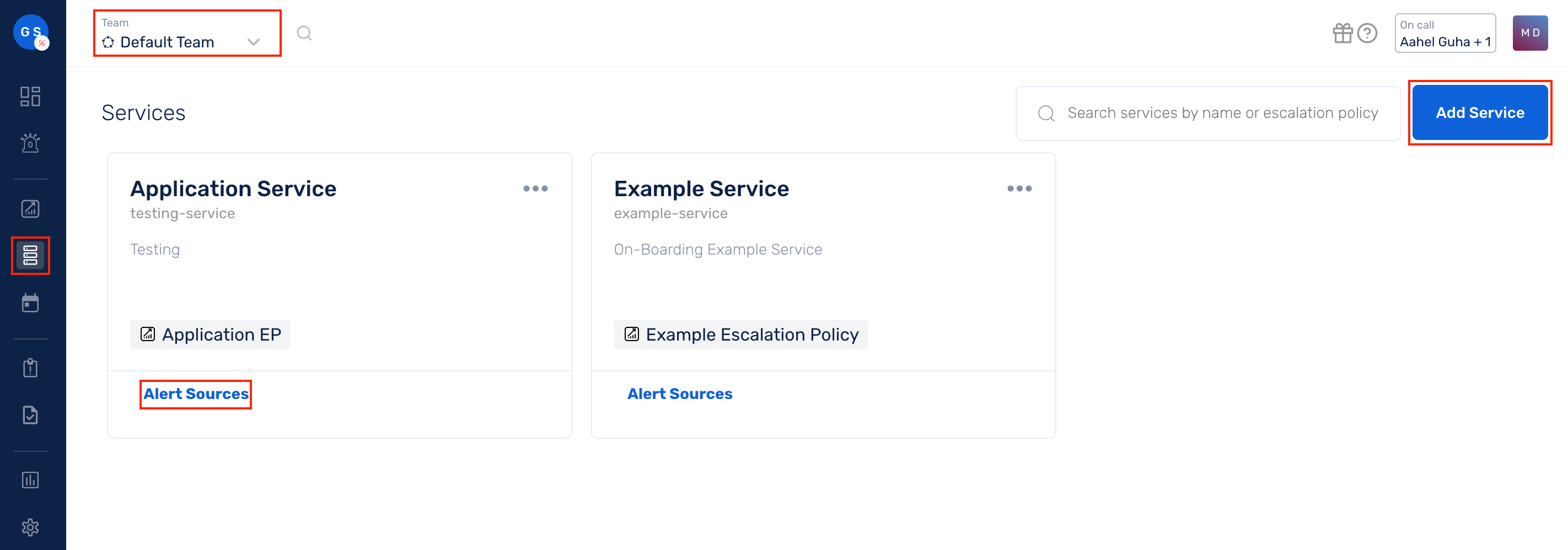
(1) From the navigation bar on the left, select Services. Pick the applicable Team from the Team-picker on the top. Next, click on Alert Sources for the applicable Service
(2) Search for Graylog from the Alert Source drop-down and copy the Webhook URL
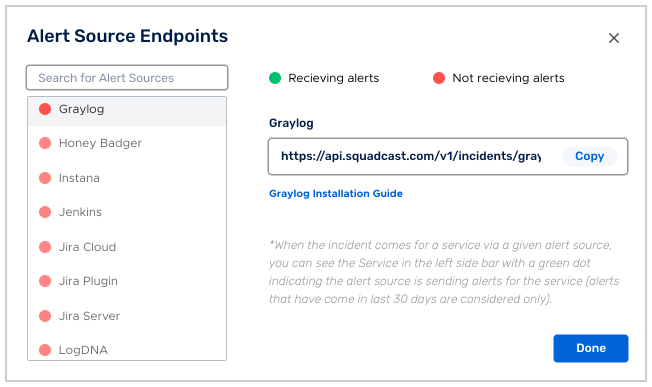
For an Alert Source to turn active (indicated by a green dot - Receiving alerts against the name of the Alert Source in the drop-down), you can either generate a test alert or wait for a real-time alert to be generated by the Alert Source.
An Alert Source is active if there is a recorded incident via that Alert Source for the Service in the last 30 days.
Create a Squadcast Webhook in Graylog
- Login to your graylog web console and go to Alert tab on the top.
- Click on Notifications.
- Click on Add new notification.
- Select All messages on Notify on Stream
- Select HTTP Alarm Callback on Notification type and click on Add alert notification.
- Give a title to the notification and put the Squadcast web hook url from the previous step on the url field and click on Save.
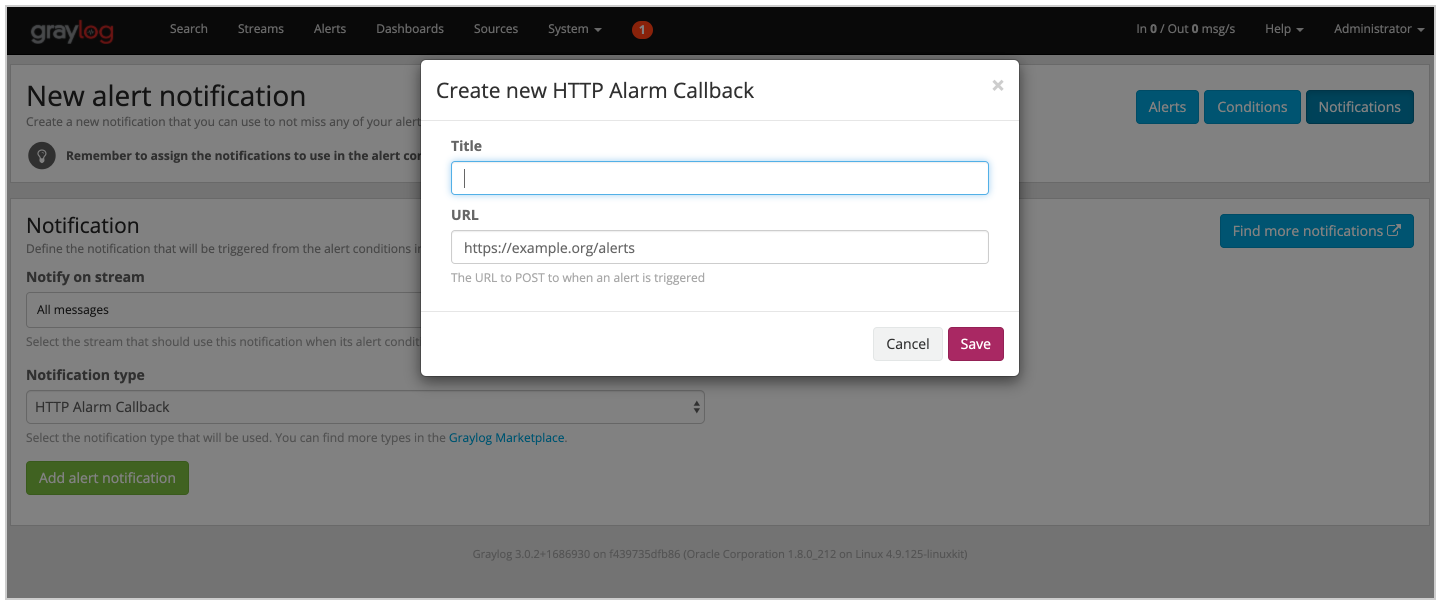
Now whenever an alert is triggered by Graylog, an incident will be created automatically in Squadcast.