Threat Stack
This document will help you integrate Threat Stack with Squadcast.
Threat Stack provides full stack cloud security observability and compliance for infrastructure and applications. Route detailed events from Threat Stack to the right users in Squadcast.
How to integrate Threat Stack with Squadcast
In Squadcast: Using Threat Stack as an Alert Source
(1) From the navigation bar on the left, select Services. Pick the applicable Team from the Team-picker on the top. Next, click on Alert Sources for the applicable Service
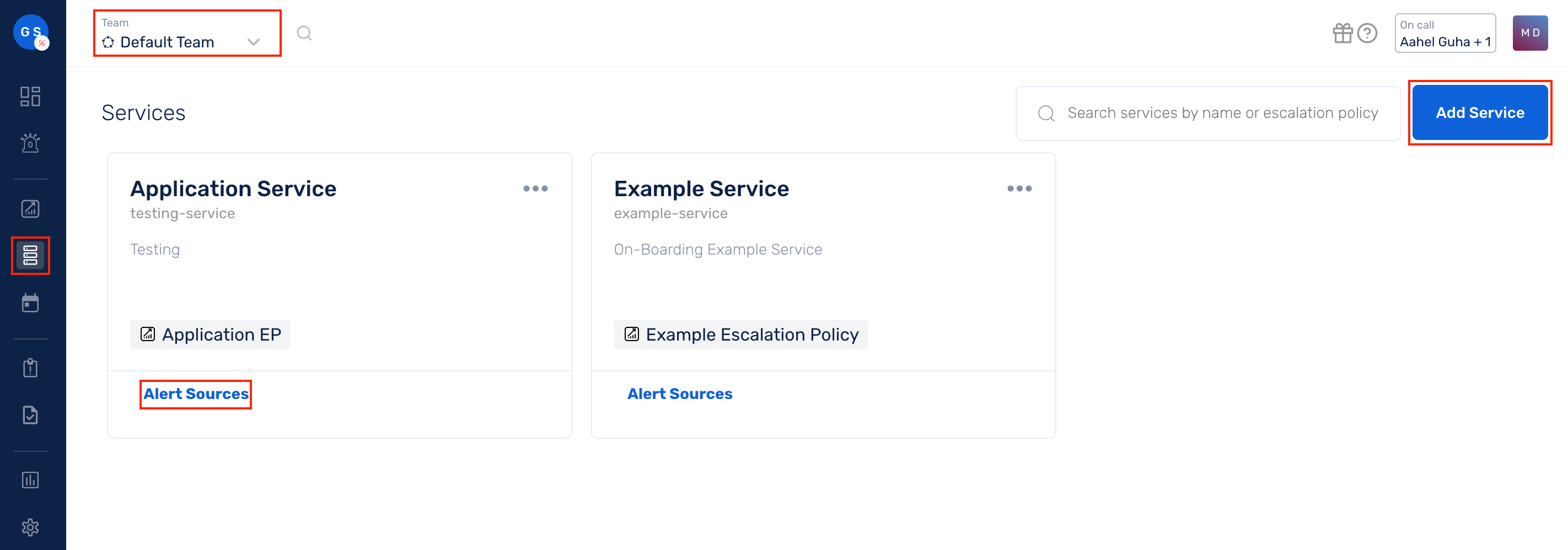
(2) Search for Threat Stack from the Alert Source drop-down and copy the Webhook URL
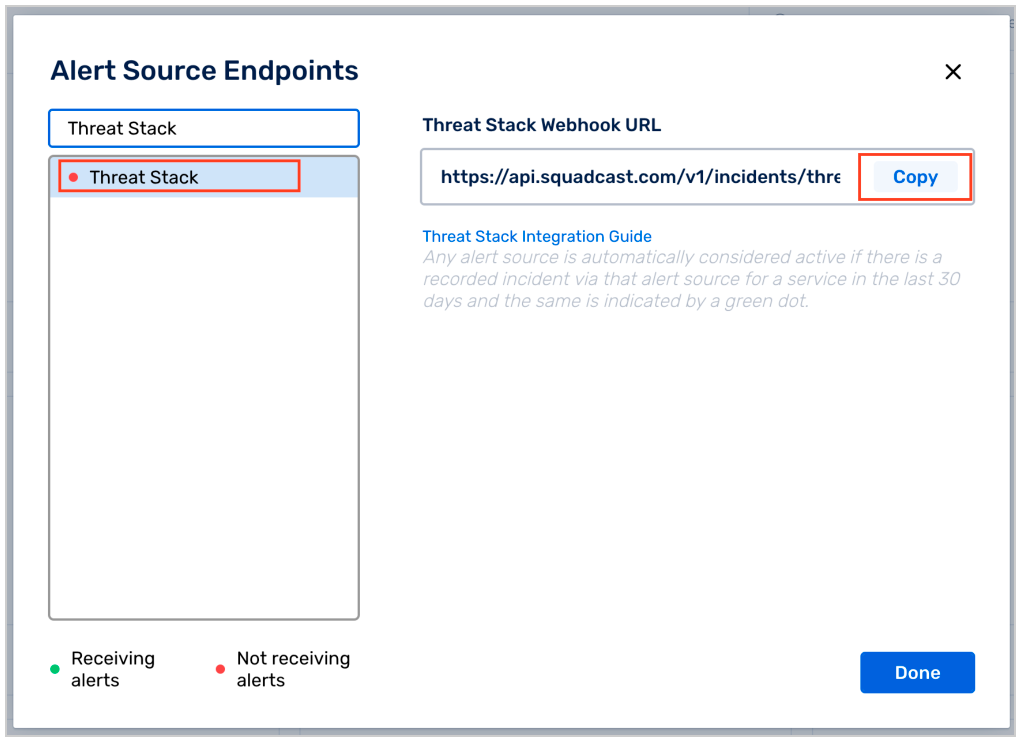
For an Alert Source to turn active (indicated by a green dot - Receiving alerts against the name of the Alert Source in the drop-down), you can either generate a test alert or wait for a real-time alert to be generated by the Alert Source.
An Alert Source is active if there is a recorded incident via that Alert Source for the Service in the last 30 days.
In Threat Stack: Create a Squadcast Webhook
(1) From the Home Page, go to Settings
(2) Select the Integrations tab
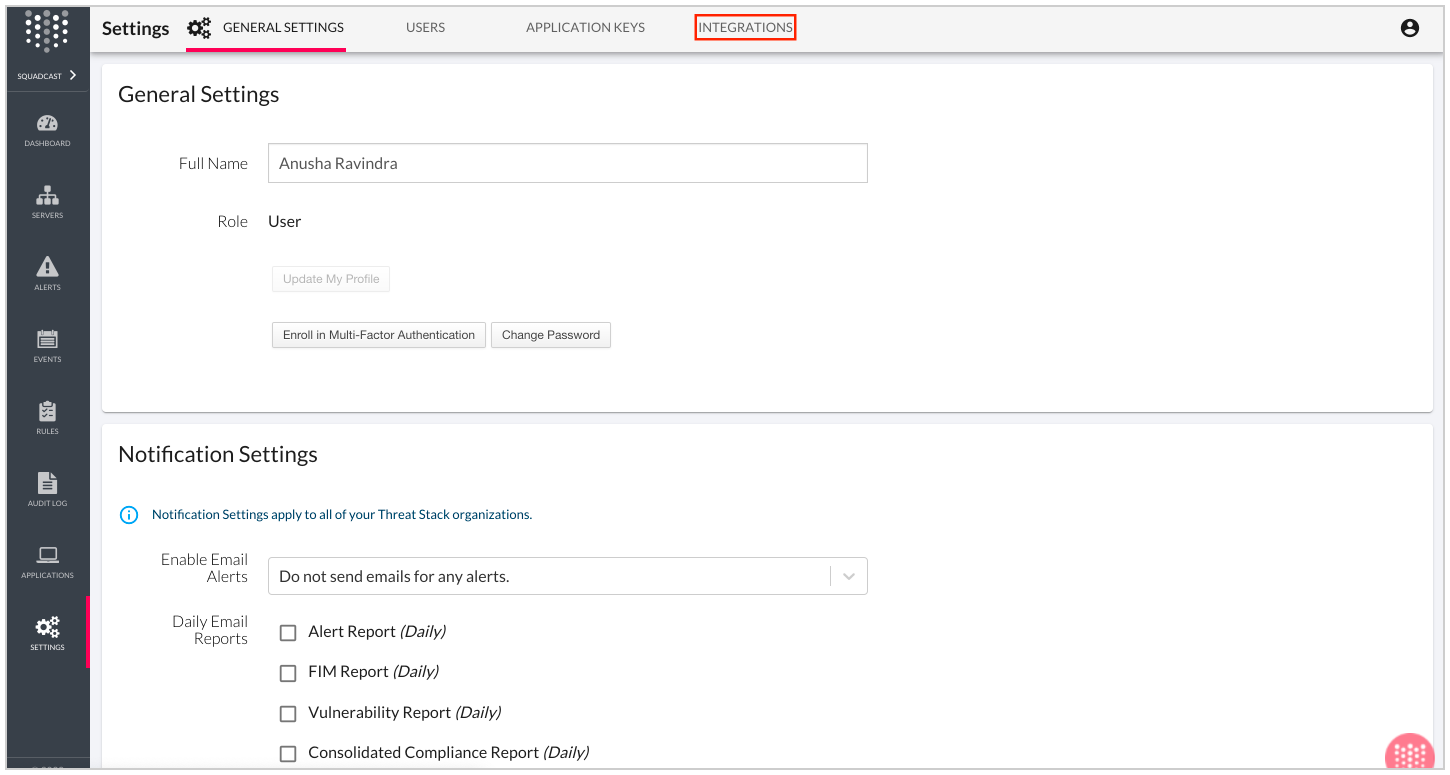
(3) Scroll below to Webhook API. Give it a Name, paste the Webhook URL copied from Squadcast under URL and pick Alert Severity from the drop down to suit your needs. Click on Save
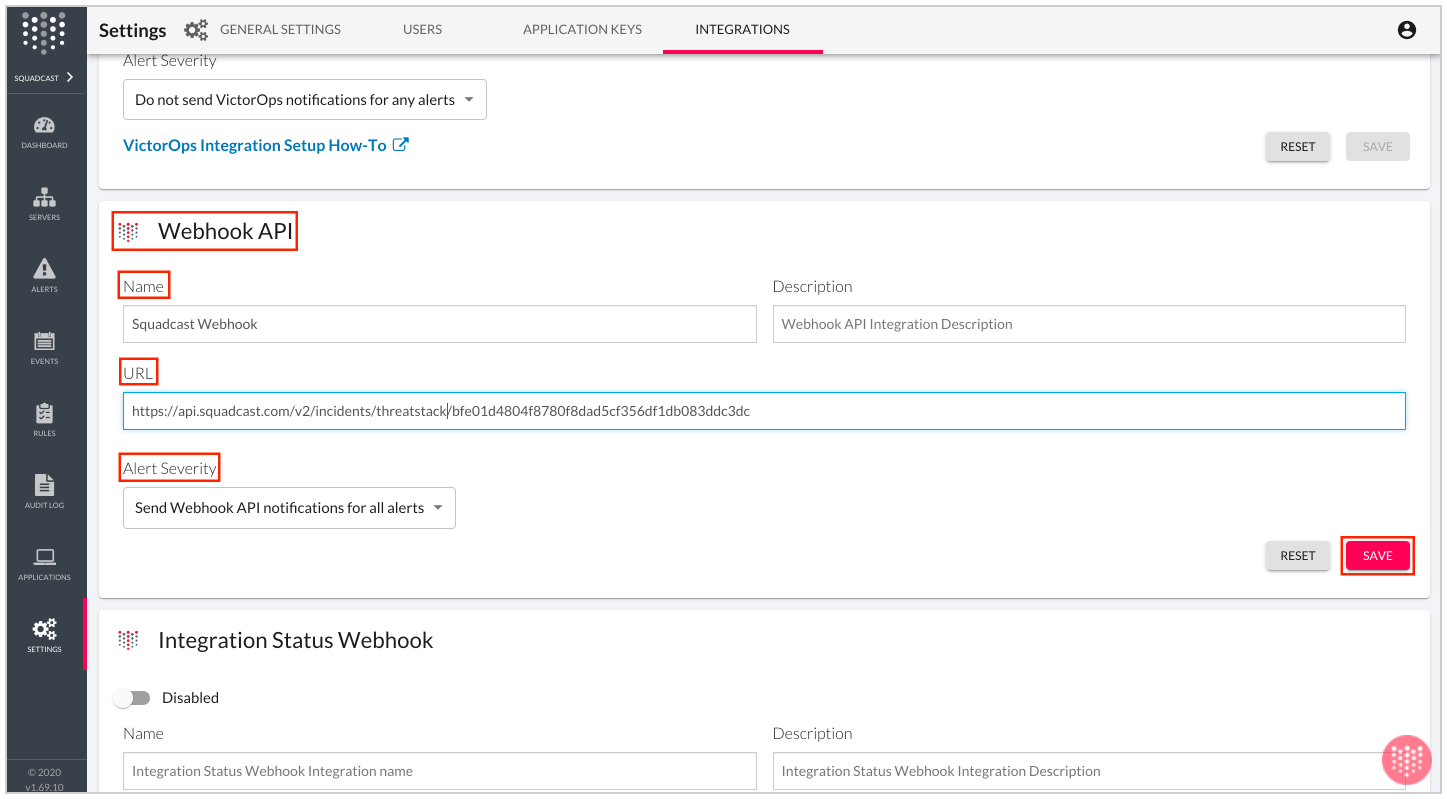
While choosing an option from the Alert Severity dropdown, in order to ensure all alerts reach Squadcast and you do not miss out on any by mistake, choose the option Fire Webhook for all alerts. This will ensure all alerts are reaching Squadcast.
Within Squadcast, you can choose how you want each of these alerts to be treated (i.e., you can choose to tag and route them to the right people based on severity, deduplicate or suppress them to control alert noise).
That is it, you are good to go! Based on the “Alert Severity” value chosen while creating the Webhook, only notifications with those severity values would be created as incidents in Squadcast. You can then manually resolve incidents in Squadcast.
- Webhook Concurrency Limit
The Threat Stack Webhook API batches alerts by severity for an organization. The Webhook API pushes the batched alerts to the customer's webhook endpoint every 10 seconds.
For example, you configure the Threat Stack Webhook API to only send you Severity 1 alerts. At 10:00:01 a.m., in the Threat Stack platform, you receive 15 alerts. Five are Severity 1 and ten are Severity 3. The Threat Stack Webhook API batches the five Severity 1 alerts and sends them to your receiving application at 10:00:10 a.m. - Configure Network Webhook Access
Ensure the following IP addresses are open in your firewall to allow the Threat Stack Webhook API to push alerts to the Squadcast Webhook:- 52.20.173.142
- 54.173.79.87
- 54.174.225.119
Q: Does this integration support auto-resolution of incidents in Squadcast?
A: No, this integration does not support auto-resolution of incidents in Squadcast since Threat Stack does not send out alert resolve notifications via the Webhook.