Splunk
This document will help you integrate Splunk with Squadcast.
Splunk is used to search, analyze and visualize the machine-generated data gathered from the websites, applications, sensors, devices etc. which make up your IT infrastructure and business. Route detailed event information from Splunk to the right users in Squadcast.
How to integrate Splunk with Squadcast
In Squadcast: Using Splunk as an Alert Source
(1) From the navigation bar on the left, select Services. Pick the applicable Team from the Team-picker on the top. Next, click on Alert Sources for the applicable Service
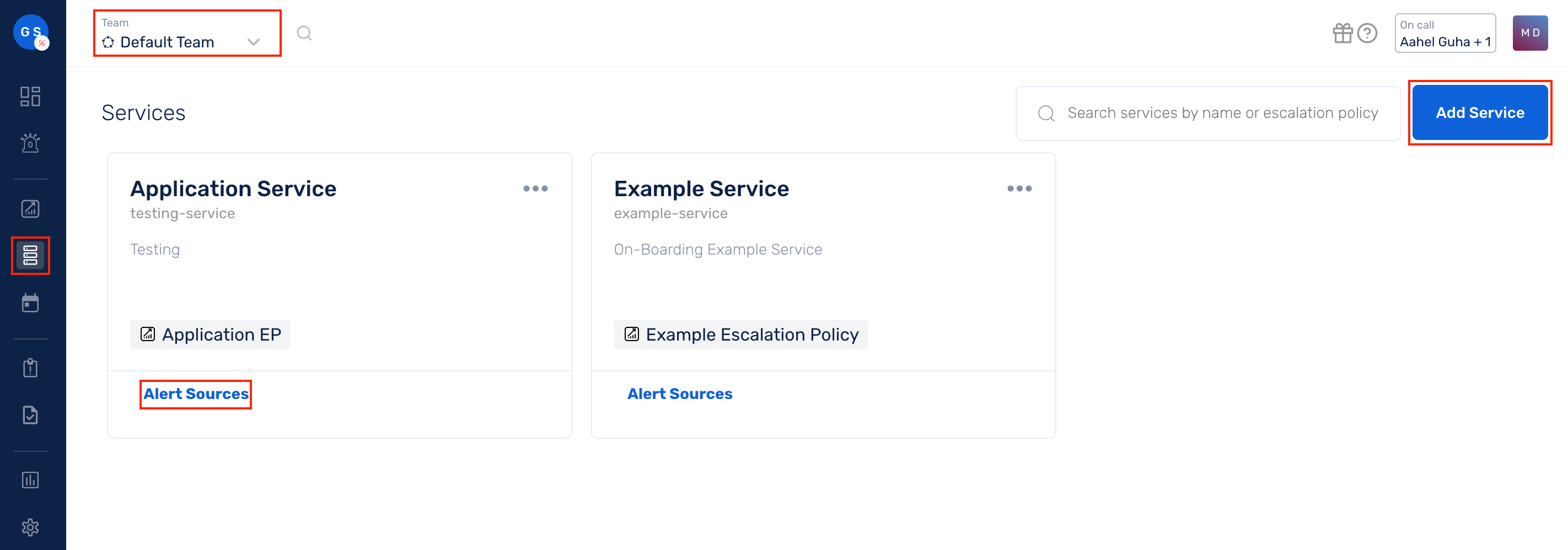
(2) Search for Splunk from the Alert Source drop-down and copy the Webhook URL
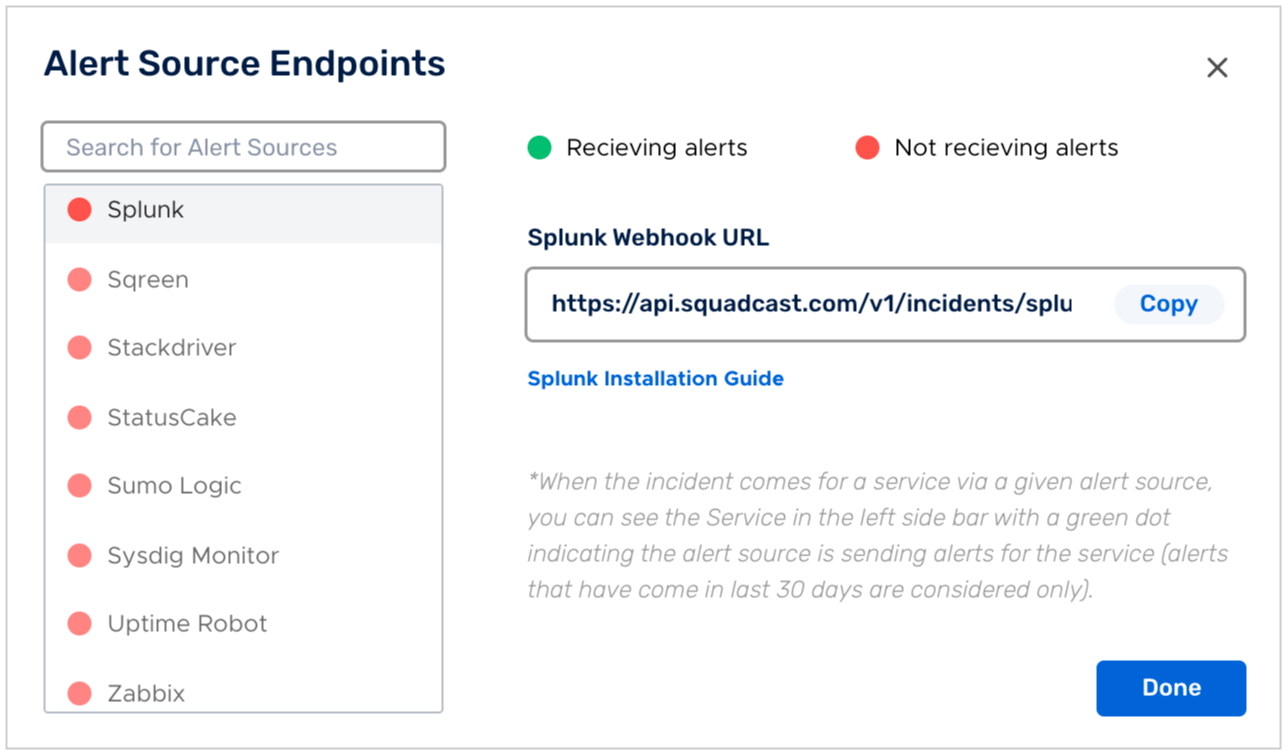
For an Alert Source to turn active (indicated by a green dot - Receiving alerts against the name of the Alert Source in the drop-down), you can either generate a test alert or wait for a real-time alert to be generated by the Alert Source.
An Alert Source is active if there is a recorded incident via that Alert Source for the Service in the last 30 days.
In Splunk: Create a Squadcast webhook alert
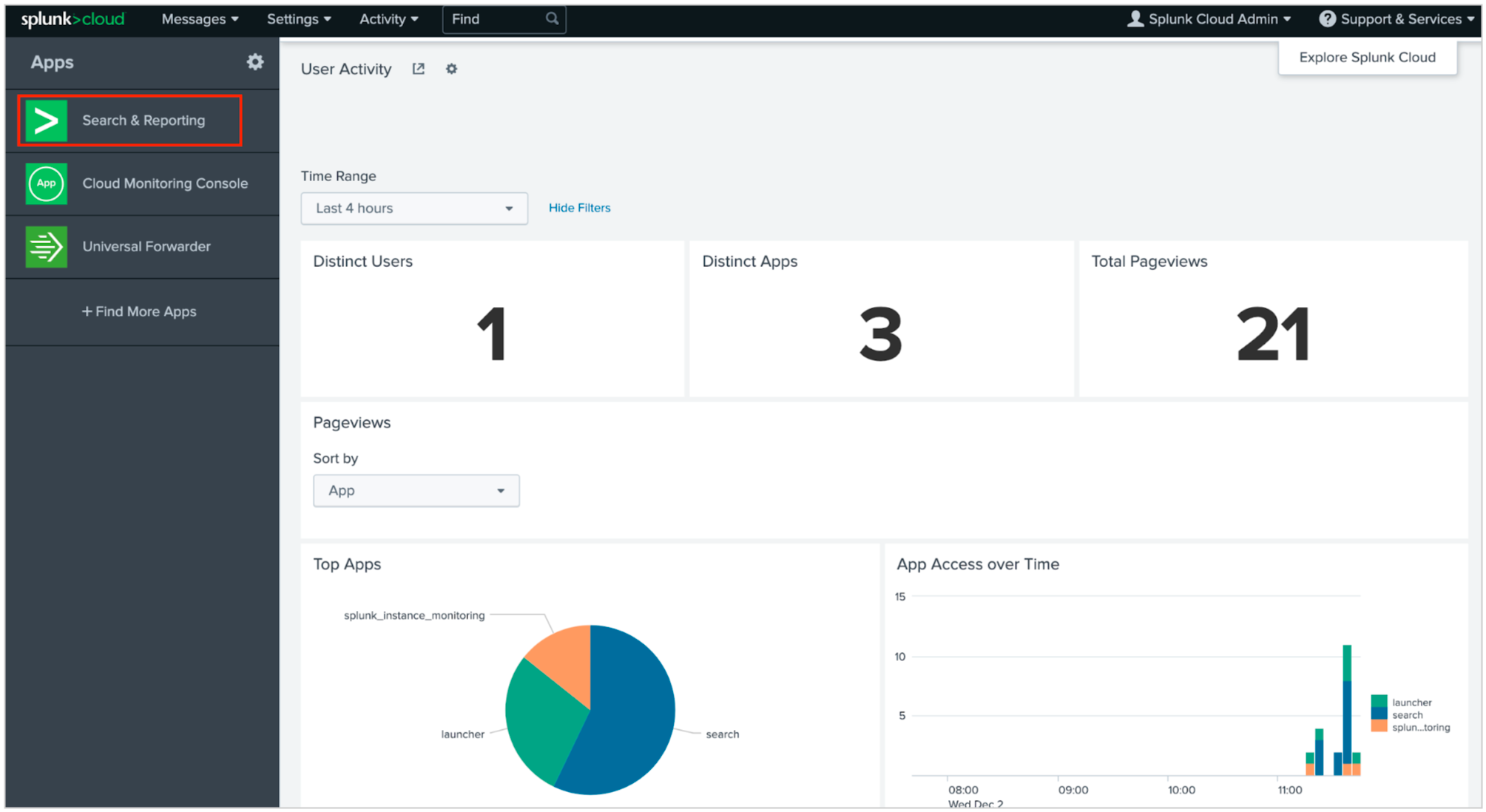
(1) In the Splunk dashboard, click on Search & Reporting under Apps
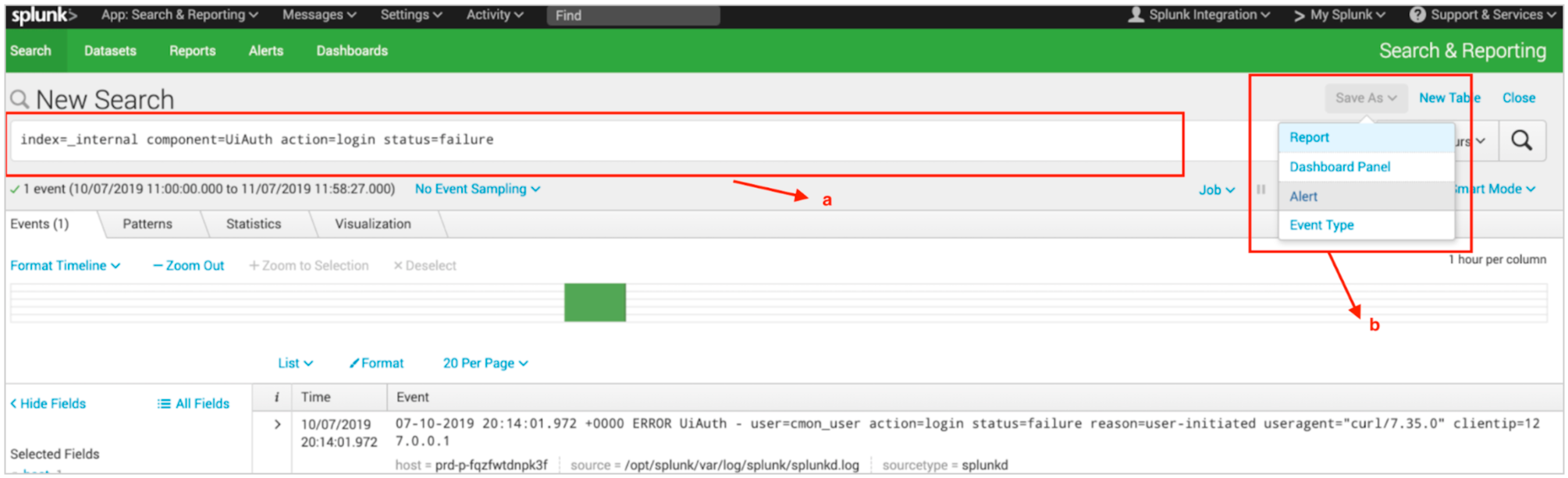
(2) Run your desired search query in the logs (a) and then click on Save As and select Alert (b)
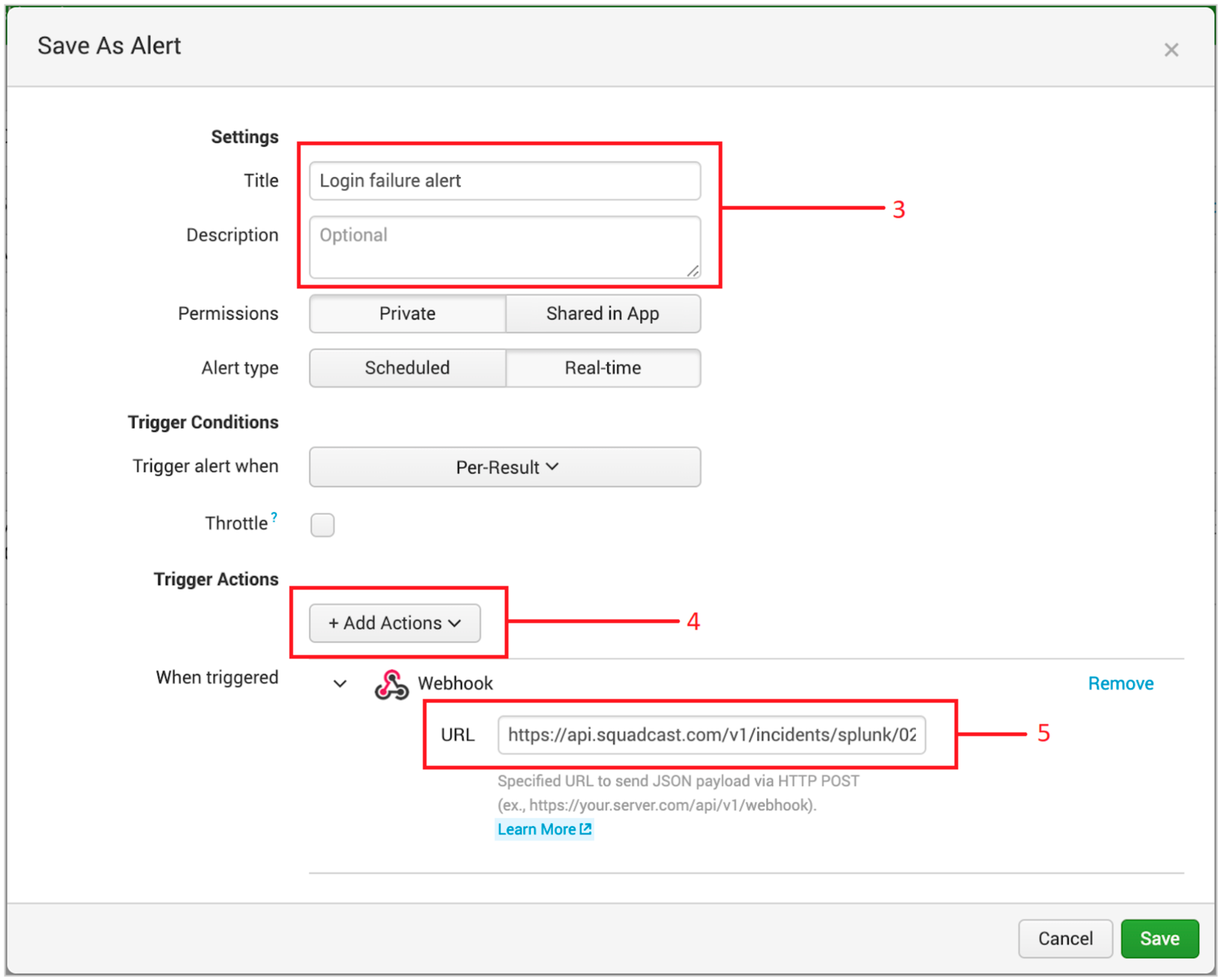
(3) In the Save As Alert box, enter the title, description and other Trigger Conditions. You can find more information on what each of these parameters mean in the Splunk documentation.
(4) Under Trigger Actions, click on Add Actions and select Webhook
(5) Paste the copied webhook URL from Squadcast under URL and click on Save
That’s it! Your Splunk Integration is now complete. Whenever an alert is fired for your search query, an incident will be created in Squadcast.
FAQ
Q: If an alert gets resolved in Splunk, does Splunk send auto-resolve signals to Squadcast?
A: No, Splunk does not send auto-resolve signals to Squadcast. Hence, Squadcast incidents from Splunk should be resolved manually.